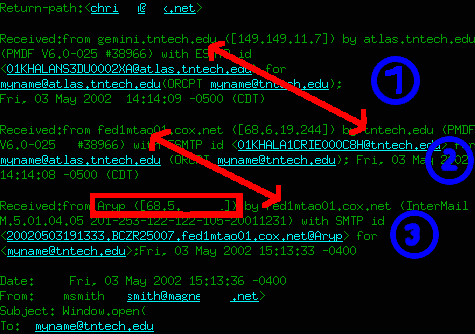
- is the internal transfer betwen internal mail hosts. This can be
verified using the "host" command:
$ host -t mx tntech.edu
tntech.edu mail is handled (pri=10) by gemini.tntech.edu
tntech.edu mail is handled (pri=20) by eagle.tntech.edu
-
is the transfer from a remote mail system to the (external) local host.
This is one place to look for the remote host, since anithing beyond this
may be forged.
Here you can read the remote sender-side identification and it's real host
name by reverse DNS (as long as it's enabled and the name is available).
The host name matches the IP, so we can look at the next header:
$ host 68.6.19.224
Name: fed1wml01.mgt.cox.net
Address: 68.6.19.224
-
is the remote system. It's usurally the mail server from the provoider the
sender uses, but it may also be an open relay or completely fake.
Here, the sender-side identification is not an existing host name.
This is not unusural for the first server in the chain.
The IP of the sender is in the same network as this server:
$ host 68.5.xxx.xxx
Name: ip68-5-xxx-xxx.oc.oc.cox.net
Address: 68.5.82.141
Aliases:
With the time and the IP, cox.net can locate the sender.